Iot ssh over ssh
Reverse SSH tunneling is a technique used to establish a secure connection from a remote server or a remote IoT device back to a local machine. Instead of connecting from a local machine to a remote server, iot ssh over ssh, as in traditional SSH connections, reverse SSH tunneling establishes a connection from the remote server to the local machine.
These tips will help you safeguard your IoT and keep it safe from unauthorized access. Here are some security considerations to keep in mind when using SSH for remote access to your IoT device:. It is critical to change the default password to a strong and unique one as soon as possible to prevent unauthorized access. Use strong authentication credentials: Use strong and unique usernames and passwords for all user accounts on your IoT device, including the regular user account you use to log in via SSH. Avoid using easily guessable usernames or weak passwords, and consider using a password manager to generate and store complex passwords securely. This includes installing security updates and patches for the OS and SSH software as they become available.
Iot ssh over ssh
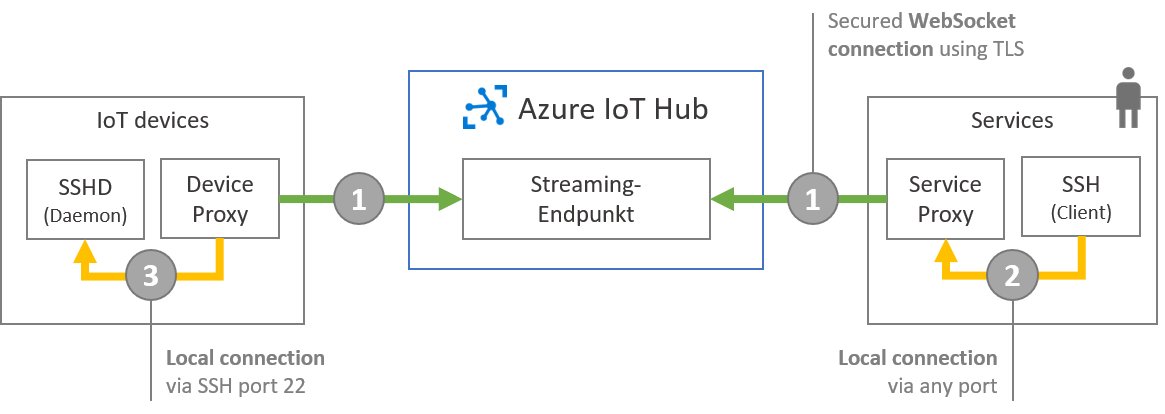
This content cannot be displayed without JavaScript. Please enable JavaScript and reload the page. It can be used to access endpoints that are protected by a firewall or to add encryption to an otherwise unencrypted channel. A connection managed within the Things service supports establishing an SSH tunnel local port forwarding to connect to the target endpoint. You can enable and configure it in the connection management section of the Things UI. Once configured, Things service takes care of creating a tunnel and connecting to it, in order to establish a connection to the actual endpoint. The state of the tunnel is reported in the connection logging section in the UI. This can be very helpful to diagnose connectivity problems. The credentials used to authenticate at the SSH server. Things supports password authentication and public key authentication.
Try our demo for Video Surveillance? SSH uses encryption to secure the connection between two devices. On both ends client and embedded deviceyou just download, configure and run the existing applications.
Thankfully, you can navigate around this by setting up an SSH tunnel. This is widely used in and outside of the IoT community. Is there an even better solution for IoT devices? Book a consultation today and get help with tech support, business inquiries, and other IoT queries. We are happy to help. Talk to you soon.
You can use the quick setup or the manual setup method for creating a tunnel. This tutorial shows how to open a tunnel using the quick setup method and use the browser-based SSH to connect to the remote device. For an example that shows how to open a tunnel using the manual setup method, see Open a tunnel using manual setup and connect to remote device. Using the quick setup method, you can create a new tunnel with default configurations that can be edited. A web-based local proxy is configured for you and the access token is automatically delivered to your remote destination device using MQTT.
Iot ssh over ssh
These tips will help you safeguard your IoT and keep it safe from unauthorized access. Here are some security considerations to keep in mind when using SSH for remote access to your IoT device:. It is critical to change the default password to a strong and unique one as soon as possible to prevent unauthorized access. Use strong authentication credentials: Use strong and unique usernames and passwords for all user accounts on your IoT device, including the regular user account you use to log in via SSH. Avoid using easily guessable usernames or weak passwords, and consider using a password manager to generate and store complex passwords securely. This includes installing security updates and patches for the OS and SSH software as they become available. A Use SSH key-based authentication : Instead of relying solely on password-based authentication, it is recommended to use SSH key-based authentication, which is more secure. Then disable password-based authentication in SSH configuration to prevent brute-force attacks. Follow SSH key management best practices and understand its limitations.
Vnl 2023 womens
IoT remote access to IoT devices allows administrators to address unauthorized activity before any damage is done. Conclusion and Alternatives. We strive to build future-proof and safe communications for businesses and organizations to grow safely in the digital world. It is highly recommended to enable validation of the SSH host in productive systems. If you use this setup method, you must configure the local proxy on your source device. Regularly review logs to detect and respond to potential security threats in a timely manner. Open a tunnel and start SSH session to remote device. Ideally, one root-level password should be used per server, and a root access account should only be utilized locally for IT maintenance and troubleshooting. Credentials The credentials used to authenticate at the SSH server. Local port forwarding connects local users to remote devices and servers on a different network, whereas remote port forwarding works the opposite way, granting remote networks access to a local server or device. Host validation It is highly recommended to enable validation of the SSH host in productive systems.
Welcome to the world of IoT devices! As technology continues to advance, we find ourselves surrounded by a myriad of interconnected devices that make our lives easier and more convenient. From smart speakers to wearable devices, IoT has become an integral part of our daily routine.
Document Conventions. Stay vigilant, follow the principle of least privilege a user or program should be given only the minimum level of access or permissions necessary to perform their job or function , and regularly review and update your security measures to ensure the highest level of protection for your IoT device and the data it contains. The term IoT refers to the devices that are connected to the internet. IoT means Internet of Things. A Use SSH key-based authentication : Instead of relying solely on password-based authentication, it is recommended to use SSH key-based authentication, which is more secure. Dynamic port forwarding involves both types of tunneling working simultaneously for inbound and outbound traffic. Leaving keys unsupervised is like publishing a list of login credentials online for everyone to see — it leaves a trail of crumbs for hackers to use to breach a vulnerable target without being flagged as an unauthorized user. Record SSH sessions , if possible, and store them in a safe location, so that they can be played back like a video and reviewed later on for compliance and auditing purposes. Host validation It is highly recommended to enable validation of the SSH host in productive systems. Yet, common shortcuts and risky backend methods can lead cybercriminals straight into a bustling network. The prerequisites for running the tutorial can vary depending on whether you use the manual or quick setup methods for opening a tunnel and accessing the remote device. You need to download, install and setup SSH server in your IoT device so that you could connect to it remotely via the internet. Enable automatic security updates: Configure your IoT device to automatically install security updates for the operating system and any software you have installed, including the SSH server. Thanks for letting us know this page needs work.

0 thoughts on “Iot ssh over ssh”