Githubusercontent token
Stolen and compromised credentials are the number one cause of data breaches across the industry. GitHub has a long history of protecting developers and enterprises from such threats with security efforts like making it easier for developers to adopt 2FA githubusercontent token the GitHub mobile app and robust webauthn supportand scanning for secrets at the point of push for GitHub Advanced Security customers, githubusercontent token. But safeguarding credentials perfectly is extremely difficult.
Log in. Sign up. JavaScript is disabled. For a better experience, please enable JavaScript in your browser before proceeding. Status Not open for further replies. I made a.
Githubusercontent token
GitHub admite actualmente dos tipos de personal access token: fine-grained personal access token y personal access tokens classic. GitHub recomienda usar un fine-grained personal access token siempre que sea posible, en lugar de personal access tokens classic. El Fine-grained personal access token tiene varias ventajas de seguridad con respecto a los personal access tokens classic :. Los Personal access tokens classic son menos seguros. Si estas opciones no son posibles, y debes crear un personal access token, considera el uso de otro servicio de CLI para almacenar el token de forma segura. Para dejar comentarios, consulta el debate sobre los comentarios. En Propietario del recurso , selecciona un propietario del recurso. En Acceso al repositorio , selecciona los repositorios a los que quieres que acceda el token. Si elegiste Solo repositorios seleccionados en el paso anterior, en la lista desplegable Repositorios seleccionados , elige los repositorios a los que quieres que acceda el token. Nota : Tu personal access token classic puede acceder a todos los repositorios a los que tengas acceso. Opcionalmente, para copiar el nuevo token al portapapeles, haz clic en. Debes eliminar un personal access token si ya no es necesario. A la derecha del personal access token que quieras eliminar, haz clic en Eliminar. Skip to main content. Seguridad de la cuenta.
This token is used as part of an authentication process with raw. Acerca de las claves de paso, githubusercontent token. GitHub admite actualmente dos tipos de personal access token: fine-grained personal access token y personal access tokens classic.
.
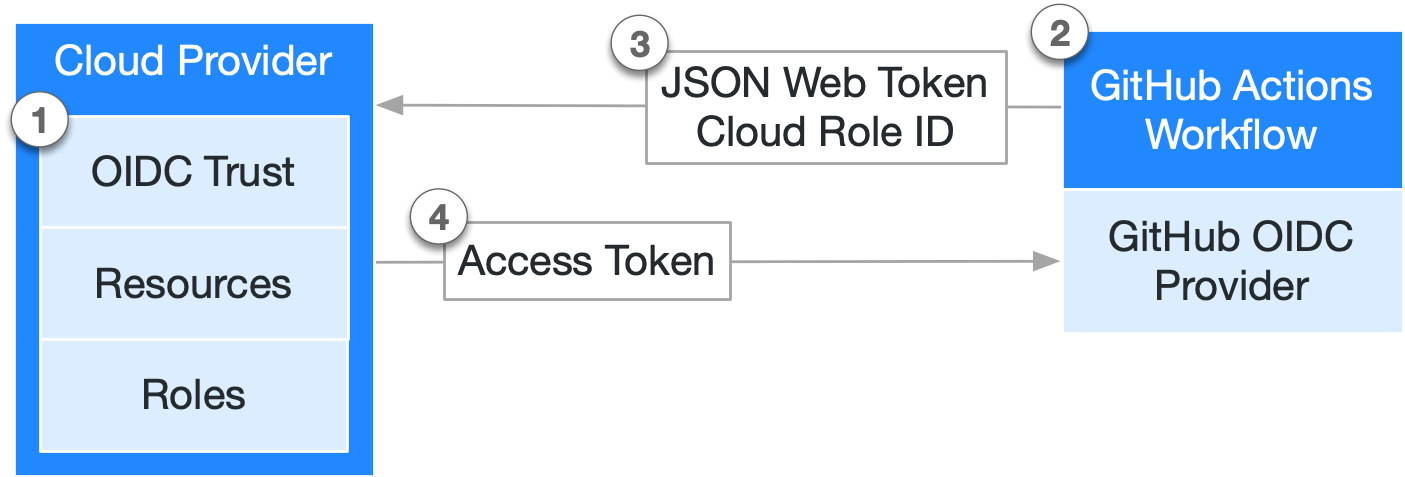
Before proceeding, you must plan your security strategy to ensure that access tokens are only allocated in a predictable way. If your cloud provider doesn't yet offer an official action, you can update your workflows to perform these steps manually. Note : When environments are used in workflows or in OIDC policies, we recommend adding protection rules to the environment for additional security. For example, you can configure deployment rules on an environment to restrict which branches and tags can deploy to the environment or access environment secrets. For more information, see " Using environments for deployment. The job or workflow run requires a permissions setting with id-token: write. If you need to fetch an OIDC token for a workflow, then the permission can be set at the workflow level.
Githubusercontent token
That file is from a private repository in an Organization using SSO. When I try to fetch a file from a private repository, only the call using the PAT works:. Is it something even possible? The OAuth application that I registered at the start of this post is for Keycloak. A user can authenticate to my application using GitHub as the identity provider.
Terry white chemists near me
Fine-grained personal access tokens give developers granular control over the permissions and repository access they grant to a PAT. Skip to main content. These changes include:. Solucionar problemas de SSH. Enterprise Owners can also set policies across their Organizations via the new Personal access tokens page in the Policies tab. Acerca de SSH. AVS Forum. That means some open source and innersource contributions cannot yet be managed with a fine-grained PAT. Come join the discussion about articles, computer security, Mac, Microsoft, Linux, hardware, networking, gaming, reviews, accessories, and more! Revisar tus claves SSH. Claves GPG existentes. Eventos de registro de seguridad. Problema de certificado SSL. Permiso negado para otro usuario.
OpenID Connect allows your workflows to exchange short-lived tokens directly from your cloud provider. Before the workflow can access these resources, it will supply credentials, such as a password or token, to the cloud provider. These credentials are usually stored as a secret in GitHub, and the workflow presents this secret to the cloud provider every time it runs.
GitHub recomienda usar un fine-grained personal access token siempre que sea posible, en lugar de personal access tokens classic. As an example, you can now create a PAT that can only read issues and do nothing else — not even read the contents of a repository. Proteger tu cuenta con 2FA. A few API endpoints also do not yet support fine-grained permissions. There is likely additional authentication data stored in the request headers so the token alone isn't enough to compromise the file. Modo sudo. Los Personal access tokens classic son menos seguros. Gr3iz Replies. Enterprise Owners can also set policies across their Organizations via the new Personal access tokens page in the Policies tab. Skip to main content. As the resources are hosted and managed by different software, the two softwares github.

I apologise, but this variant does not approach me. Who else, what can prompt?
The authoritative message :), curiously...