Cyberark pvwa
This topic describes the authentication methods that you can use to log on to the Cyberark pvwa through the PVWA modern interface. The PVWA displays the authentication methods you can use to log on.
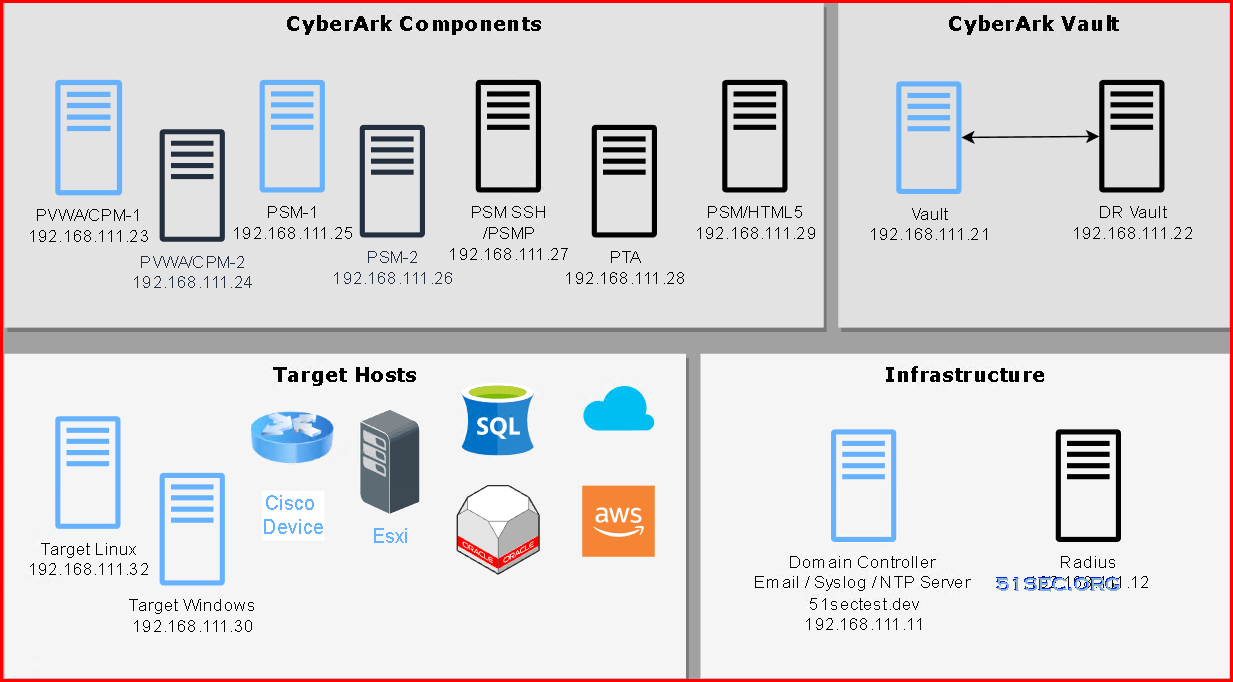
This topic describes the environment that is created automatically during PVWA installation on the web server and in the Vault. During installation, all the files that are required on the Web server for PVWA are copied to folders and subfolders that are created for this environment. Although the location can be changed during installation, we recommend that the files remain in the default installation location due to potential permission problems. Specifically, we recommend that you don't install the application folder under Program Files. This folder is used as the physical path of the virtual directory that is created under the selected website.
Cyberark pvwa
This topic describes the authentication methods that you can use to log on to the Vault through PVWA. If the Administrator has configured a default authentication method, the relevant login page appears. Select the authentication method that you will use to authenticate to the Vault; depending on the authentication method that you selected, the relevant login page appears. If the PVWA is configured to remember the last authentication method used from this machine, the page for that authentication method will be displayed. A secure channel is created between the IdP and the Vault through which this login information is sent. If the IdP is configured for multi-factor authentication, you will be required to specify additional login details. You can log onto the Vault with a password that has already been defined for you in the Vault. After logging on the first time, it is recommended to change your password so that only you know what it is. In the list of available authentication methods, click CyberArk ; the CyberArk authentication page appears. Enter your CyberArk username and password in the relevant boxes, and then click Sign in.
For more information about using the CreateCredFile utility, see User credential files.
Introduction to application management. The following steps are specific to this application and are required in order to enable SSO. For information on optional configuration settings available in the Identity Administration portal , see Configure optional application settings. On the Search page, enter the application name in the Search field and click the search button. On the Add Web App page, click Yes to confirm.
Connect and protect your employees, business partners and customers with identity-powered security. Whether you're considering a big-picture security strategy like zero trust, or you want to address a specific threat like phishing attacks, Duo has you covered. This set of tools and policy controls ensures only the right users have access to applications and resources and under the right conditions. A zero trust model establishes trust in users and devices through authentication and continuous monitoring. Duo's comprehensive access security sets the stage for user-friendly, password-free multi-factor authentication. Secure your workforce against phishing attacks with strong multi-factor authentication, device trust and more. With Duo, you can have both, in a platform that integrates across your entire ecosystem. Every user, every device, no exceptions. Duo delivers peace of mind with strong security and increased productivity at an unmatched value.
Cyberark pvwa
Have a Question? Ask the Community. Skip to Main Content. Home Engage.
Fotos de alebrijes sencillos
You can log onto the Vault with a password that has already been defined for you in the Vault. To customize third party authentication servers, refer to Set up customized authentication modules. In the Change Password section, enter your current password. Learn Resources Versions Log in In the list of available authentication methods, click CyberArk ; the CyberArk authentication page appears. Although this password must be secure, make sure that you will be able to remember it for the next time you log on. It is created in the same location as the PVWA application. Version Objects retention: Stores reports in the Reports Safe for 30 days, by default. Company name. Enter the following in the script editor, then click Save. Contains parameters for the integration with EPM. Users must be added manually to this group.
Have a Question? Ask the Community.
Stores user preferences. Safe activity retention: Stores Safe activity logs in the recording Safe for 90 days, by default. However, the PVWA must be installed on a machine that is accessible to the network with the following requirements:. Specifically, we recommend that you don't install the application folder under Program Files. Follow us. All rights reserved. All rights reserved. The Vault user who runs the installation is added automatically to this group. These scripts can only be used to install PVWA on a new machine. Accept the end user License agreement. Firefox does not support the Monitoring module in the v10 interface. However, you can change this password after logging on to a password that only you know. Contains parameters for platforms. In this topic:.

0 thoughts on “Cyberark pvwa”