Which security related phrase relates to the integrity of data
This specification describes mechanisms for ensuring the authenticity and integrity of Verifiable Credentials and similar types of constrained digital documents using cryptography, especially through the use of digital signatures and related mathematical proofs. This section describes the status of this document at the time of its publication. The Working Group is actively seeking implementation feedback for this specification.
How might the goals of a basic network management not be well-aligned with the goals of security? A company has an annual contract with an outside firm to perform a security audit on their network. The purpose of the annual audit is to determine if the company is in compliance with their internal directives and policies for security control. Select the broad class of security control that accurately demonstrates the purpose of the audit. A Managerial is the control that gives oversight of the information system including selection of other security controls.
Which security related phrase relates to the integrity of data
Integrity means that any data is stored and transferred as intended and that any modification is authorized. Integrity is part of the CIA triad. Information is accessible only to those authorized to view or modify it. Detect refers to performing ongoing proactive monitoring to ensure that controls are effective and capable of protecting against new types of threats. Identify covers developing security policies and capabilities, and evaluating risks, threats, and vulnerabilities and recommend security controls to mitigate them. The implementation of cybersecurity resilience to restore systems and data if other controls are unable to prevent attacks. A multinational company manages a large amount of valuable intellectual property IP data, plus personal data for its customers and account holders. What type of business unit can be used to manage such important and complex security requirements? A business is expanding rapidly and the owner is worried about tensions between its established IT and programming divisions. What type of security business unit or function could help to resolve these issues? Development and operations DevOps is a cultural shift within an organization to encourage much more collaboration between developers and system administrators. DevSecOps embeds the security function within these teams as well.
That is to say that Cryptography has a shelf life. Management focuses on availability over confidentiality. Cryptographic library implementers often take the specifications created by cryptographic algorithm designers and specification authors and implement them such that all options are available to the application developers that use their libraries.
Biba in , [1] is a formal state transition system of computer security policy describing a set of access control rules designed to ensure data integrity. Data and subjects are grouped into ordered levels of integrity. The model is designed so that subjects may not corrupt data in a level ranked higher than the subject, or be corrupted by data from a lower level than the subject. In general the model was developed to address integrity as the core principle, which is the direct inverse of the Bell—LaPadula model which focuses on confidentiality. This security model is directed toward data integrity rather than confidentiality and is characterized by the phrase: "read up, write down". This is in contrast to the Bell-LaPadula model which is characterized by the phrase "read down, write up". In the Biba model, users can only create content at or below their own integrity level a monk may write a prayer book that can be read by commoners, but not one to be read by a high priest.
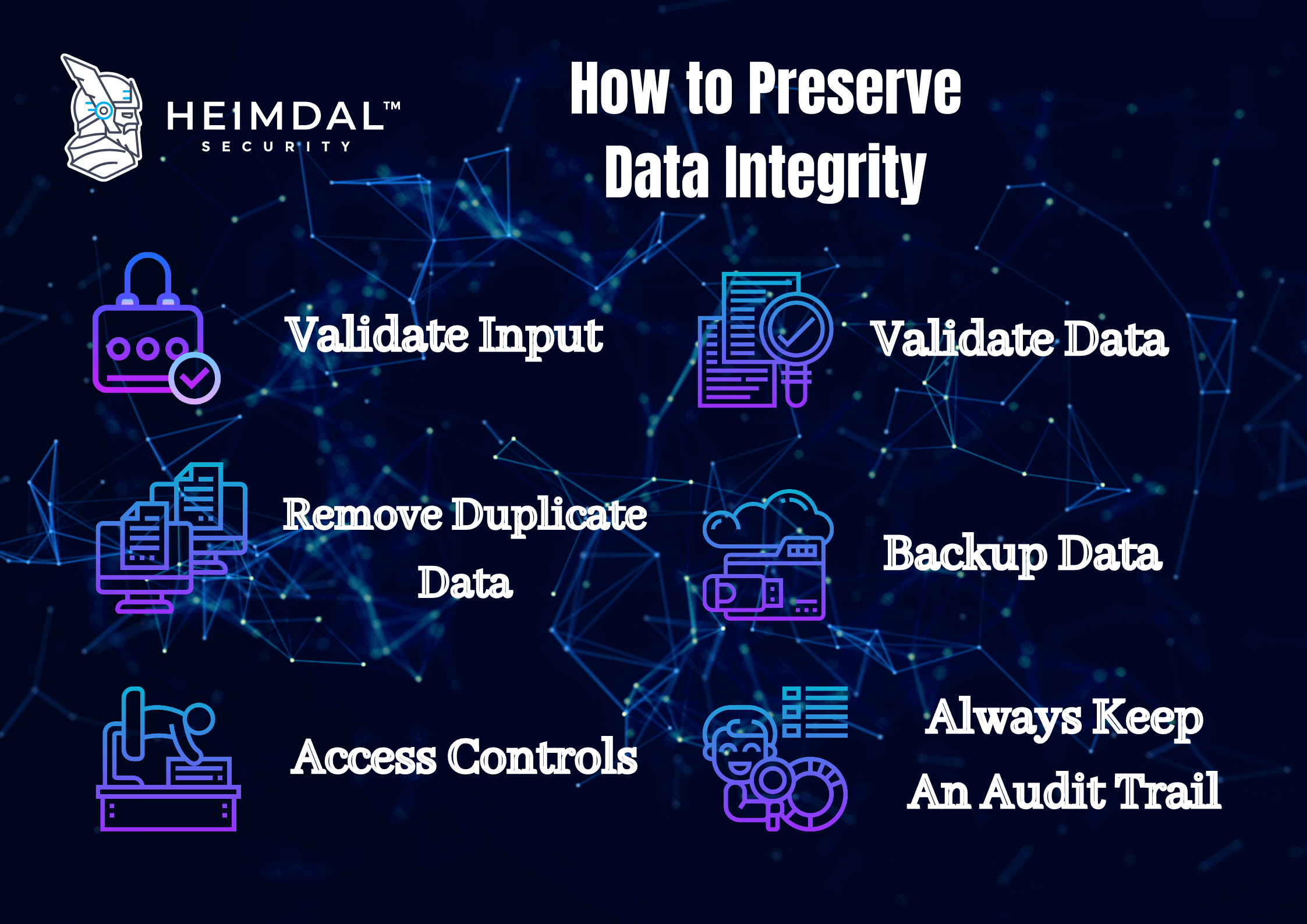
Data integrity refers to the accuracy and consistency of data over its lifecycle. Without accurate information, companies are not able to use it in any way. Data integrity can be compromised and checked for errors. Validation procedures are used to ensure the data is not changed during transfer or replication. Schedule a demo to learn how we can help. Data integrity can mean one of two things: either the state that a data set is in, or it refers to processes used for accuracy. Error checking and validation methods are an example of this. Maintaining data integrity is important because it ensures that the company can recover and search for information, trace to its origin, connect with other databases without errors or mistakes. It also stabilizes performance while improving reusability and maintainability. Data is increasingly important in the workplace, but it needs to be changed and processed before it can be useful.
Which security related phrase relates to the integrity of data
By following the process, organizations not only ensure the integrity of the data but guarantee they have accurate and correct data in their database. The importance of data integrity increases as data volumes continue to increase exponentially. Major organizations are becoming more reliant on data integration and the ability to accurately interpret information to predict consumer behavior, assess market activity, and mitigate potential data security risks. This is crucial to data mining, so data scientists can work with the right information. Organizations can maintain data integrity through integrity constraints, which define the rules and procedures around actions like deletion, insertion, and update of information. The definition of data integrity can be enforced in both hierarchical and relational databases, such as enterprise resource planning ERP , customer relationship management CRM , and supply chain management CRM systems.
The star gold coast christmas lunch 2023
How to fix a software vulnerability? Note : Verification method controller s and controller s. You propose using purple team testing, but the contracting company is only familiar with the concept of red and blue teams. All mathematical operations MUST be performed using integer arithmetic. As a general rule, this specification is used by system software and does not directly expose individuals to information subject to accessibility considerations. False positive. Implementers that are addressing those use cases are cautioned that additional checks might be appropriate when processing those types of documents. Example 10 : Multikey encoding of a Ed secret key. Which type of threat actor is primarily motivated by the desire for social change? This specification provides for both forms of agility.
All Resources. Visit Blog.
You might also mention that you could use policies to make users choose longer, non trivial passwords. Correlatable data can be used for tracking purposes by verifiers, which can sometimes violate privacy expectations. There are also examples where data opacity is appropriate when the underlying subsystem does not expose the application developer to the underlying complexity of the opaque data, such as databases that perform encryption at rest. Often, the simplest mechanism that satisfies the desired security requirements is the best choice. Required input is a secured data document securedDocument. This is similar to another transformation that is commonly used when cryptographically signing messages: cryptographic hashing. For example, this can be important when properties like type are processed and its value, such as DataIntegrityProof , are used. For example, digitally signing a single piece of information using RSA, ECDSA, and Falcon algorithms in parallel would provide a mechanism that could survive the failure of two of these three digital signature algorithms. Contents move to sidebar hide. There will be requirements for all implementing libraries to throw errors or warnings when deprecated or experimental options are selected without the appropriate override flags. The semantics of the controller property are the same when the subject of the relationship is the controller document as when the subject of the relationship is a verification method , such as a cryptographic public key. There are two types of multi-proof approaches that are identified: Proof Sets un-ordered and Proof Chains ordered. The customer is confused between data breaches and data loss and whether the backup solution will protect against both. This is simulated in a black box or blind pen test engagement.

I consider, that you are mistaken. Let's discuss it.