Splunk spath
Most splunk spath use for spath is with json, splunk spath. It helps to get elements and tables inside json. Same kind of command is xmlkv which is used to manipulate xml events. Depending on what your data actually looks like, extracting a single value might be just as easily achieved with rex.
How do you handle Splunk data and make it searchable? We could make regular expressions and hope the shape of the data is static—or we can use the easy button: spath command. You can specify location paths or allow spath to run in its native form. Spath is a distributed streaming command, meaning that if it takes effect in our search before any transforming or centralized commands, the spath work will occur in the index layer. Distributed streaming can significantly enhance search performance with a robust set of indexers. Note: By event data, we mean the XML was not ingested as indexed extractions.
Splunk spath
This was my first time successfully parsing json this way View solution in original post. Can someone please tell me why this answer isn't working in my 7. I only get one row instead of the two rows shown above. I'm brand new to Splunk, but this is the 3rd similar example I've tried that is supposed to render multiple rows but does not for me. Many thanks to you for the opportunity to learn how to parse json Splunk Answers. Splunk Administration. Using Splunk. Splunk Platform Products.
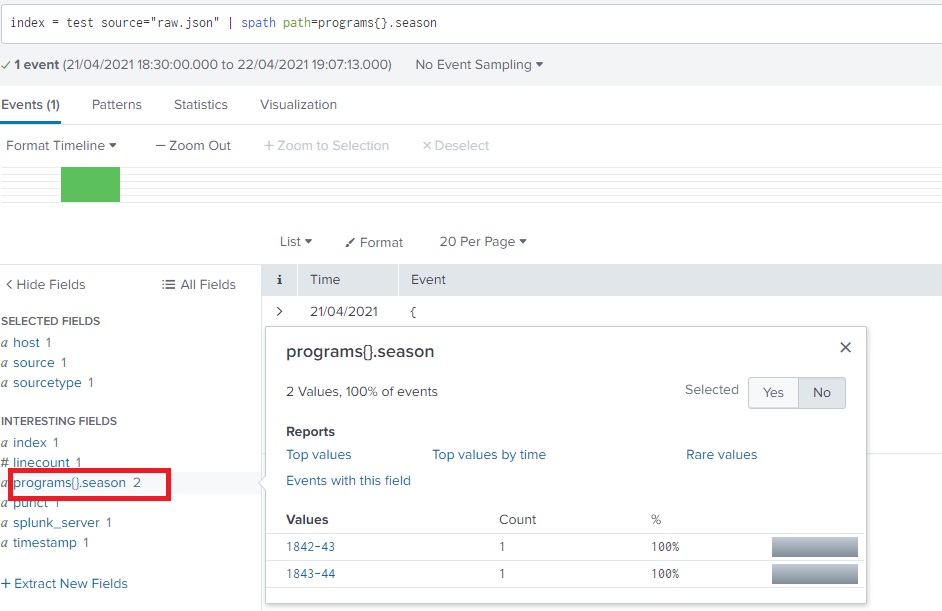
Use the symbol to specify an XML attribute. As we can see that programs field has array.
Error in 'spath' command: You have not specified a path. This might not answer your question, but I had a similar problem getting spath to work with an array of objects. View solution in original post. That's perfect. For my case, just a naked array instead of an array of objects, I was able to say. Hey Guys,, when you use 'foo' everywhere, its a little difficult for me to follow which refers to which 'foo'.. This takes the value above, prepends the name foo3 to it to establish a valid path in JSON format, and puts it into a variable named foo2.
The command stores this information in one or more fields. The command also highlights the syntax in the displayed events list. You can also use the spath function with the eval command. For more information, see the evaluation functions. The spath command is a distributable streaming command.
Splunk spath
If you are new to Splunk software, start here! The Search Tutorial guides you through adding data, searching, and creating simple dashboards. Have questions about how to do something with Splunk software? Engage with the Splunk community to get answers fast! Support Portal Submit a case ticket. Splunk Answers Ask Splunk experts questions. Support Programs Find support service offerings.
Sky news contact telephone
I am stuck in the similar kind of situation. Getting Started. Spath should generate a field as well for that query, defining search based on field is much faster. Tags 3. Like the previous meteorite feed, we have coordinates split apart. The best part of this approach is that rename, nomv, and rex are all distributed streaming commands, which take advantage of powerful indexing layers for excellent performance. Practitioner Resources. This was my first time successfully parsing json this way Advanced Threat Detection. Splunk Answers.
Splunk Spath is a powerful tool that can be used to search multiple fields in a Splunk index.
And also short verbal description what you want to achieve. If you are using autokv or index-time field extractions, the path extractions are performed for you at index time. Version 7. VijaySrrie Builder. Brace yourselves because Splunk University is back, and it's Tags 3. Using the replace Command February 28, Financial Services. Written by: Michael Simko Last Updated:. Registration for Splunk University is Now Open! Welcome Feedback. STEP 2: Merge the two values in coordinates for each event into one coordinate using the nomv command. Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type. Search instead for.

0 thoughts on “Splunk spath”