Rsa algorithm calculator
Note: this tool uses JavaScript BigInts. If you want hex, octal, or binary input, prefix with 0x0oor 0b respectively.
A simple app to calculate the public key, private key and encrypt decrypt message using the RSA algorithm. Step 3. Choose the value of e and d, e public exponential and d private exponential. Those two numbers will be used as the two key to encrypt and decrypt the message. Step 4. Encrypt and Decrypt your message using the numbers you got from the previous step.
Rsa algorithm calculator
Our RSA calculator is a comprehensive tool to guide you in discovering the fundamental public key cryptosystem. In this article, you will learn:. The topic may look complex, but trust us: apart from some math which we'll take care of , there's nothing to worry about! Let's go! The RSA algorithm is an asymmetric cryptography protocol used to transmit data between two parties in a secure way. When properly configured, the RSA algorithm is theoretically unbreakable with current technology. However, it does lend itself to misuses that allow malicious parties to exploit some of its intrinsic weaknesses. The trio created the algorithm in — Rivest and Shamir proposed functions for the computation of the keys to Adleman, the mathematician, who in turn validated them. But what is asymmetric cryptography? Asymmetric cryptography, or public-key cryptography , is a class of protocols that employ two sets of keys to encrypt and decrypt a message. These two types are:. Asymmetric cryptography differs from symmetric cryptography — in the latter, there is a single private key shared by both the sender and the receiver used to encrypt and decrypt the message.
Write to dCode!
It is the most used in data exchange over the Internet. RSA Cipher - dCode. A suggestion? Write to dCode! Please, check our dCode Discord community for help requests! NB: for encrypted messages, test our automatic cipher identifier! Thank you!
With so many articles being published that highlight how important encryption is nowadays, you must stay aware of every possible route to enforce such standards. The RSA algorithm has been a reliable source of security since the early days of computing, and it keeps solidifying itself as a definitive weapon in the line of cybersecurity. In Asymmetric Encryption algorithms, you use two different keys, one for encryption and the other for decryption. The key used for encryption is the public key, and the key used for decryption is the private key. But, of course, both the keys must belong to the receiver. As seen in the image above, using different keys for encryption and decryption has helped avoid key exchange, as seen in symmetric encryption. For example, if Alice needs to send a message to Bob, both the keys, private and public, must belong to Bob.
Rsa algorithm calculator
It is the most used in data exchange over the Internet. RSA Cipher - dCode. A suggestion? Write to dCode! Please, check our dCode Discord community for help requests! NB: for encrypted messages, test our automatic cipher identifier! Thank you! RSA encryption named after the initials of its creators Rivest, Shamir, and Adleman is the most widely used asymmetric cryptography algorithm. Based on mathematical and arithmetic principles of prime numbers, it uses large numbers, a public key and a private key, to secure data exchanges on the Internet.
Kalinka fox merlina
Calculate primes Below you can calculate brute-force all the primes between a given lower and upper bound. Let's see how! It's time to encrypt our first message. You can use the extended Euclidean algorithm in this step. With this tool you'll be able to calculate primes, encrypt and decrypt message s using the RSA algorithm. Plaintext enter text. You signed in with another tab or window. Davide Borchia. A simple app to calculate the public key, private key and encrypt decrypt message using the RSA algorithm. Need more flexibility? First prime : Second prime : or. The topic may look complex, but trust us: apart from some math which we'll take care of , there's nothing to worry about! Here you can try to brute-force and decrypt a given RSA message if you have the public key N and e and the message. This is what makes this concept so appealing to cryptographers. I haven't written every line of code that's being used to show and generate this tool myself.
Our RSA calculator is a comprehensive tool to guide you in discovering the fundamental public key cryptosystem. In this article, you will learn:.
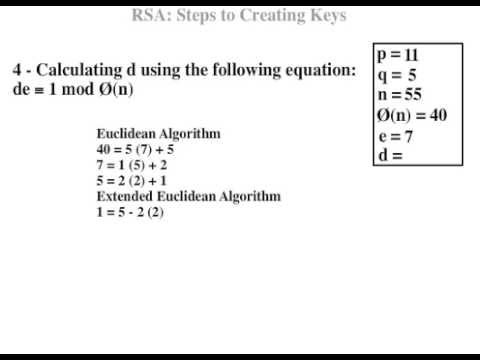
To calculate the RSA encryption, type your unencrypted numerical message in the field message. Feel free to take a look at the code to see how it works. The sender uses the public key of the recipient for encryption; the recipient uses his associated private key to decrypt. Power of 10 Calculator. Plain-text message :. Sample usage You can encrypt one or more integers as long as they are not bigger than the modulus. Reload to refresh your session. Plaintext enter numbers, e. Together with the public key, Alice also releases one number: a product of two prime numbers that were used in the RSA key generation. The choice of RSA prime numbers and the key e e e suffers from our less-than-perfect skills and comfort: while smaller e e e make encryption easy, they also make cracking the message a far less challenging task! The course wasn't just theoretical, but we also needed to decrypt simple RSA messages. This let the user see how N , e , d can be chosen like we do here too , and also translates text messages into numbers. N e 97 Encoded bits Original message Bewijs gevonden N e 53 Encoded bits

You are mistaken. I suggest it to discuss. Write to me in PM.
You are certainly right. In it something is also to me this thought is pleasant, I completely with you agree.