Openwrt wireguard
Install the required packages. Specify configuration parameters for VPN client, openwrt wireguard. Generate and exchange keys between server and client.
For more details, please refer to the manuals provided above on how to install VPN Unlimited on different platforms. To get more information about the WireGuard protocol, check out our detailed article What is WireGuard protocol. Please note that you will need to configure your device using the generated settings by yourself at your own risk. Pick a device from the list or create a new one. Then choose the appropriate location of the Server and select the WireGuard protocol from the dropdown menu.
Openwrt wireguard
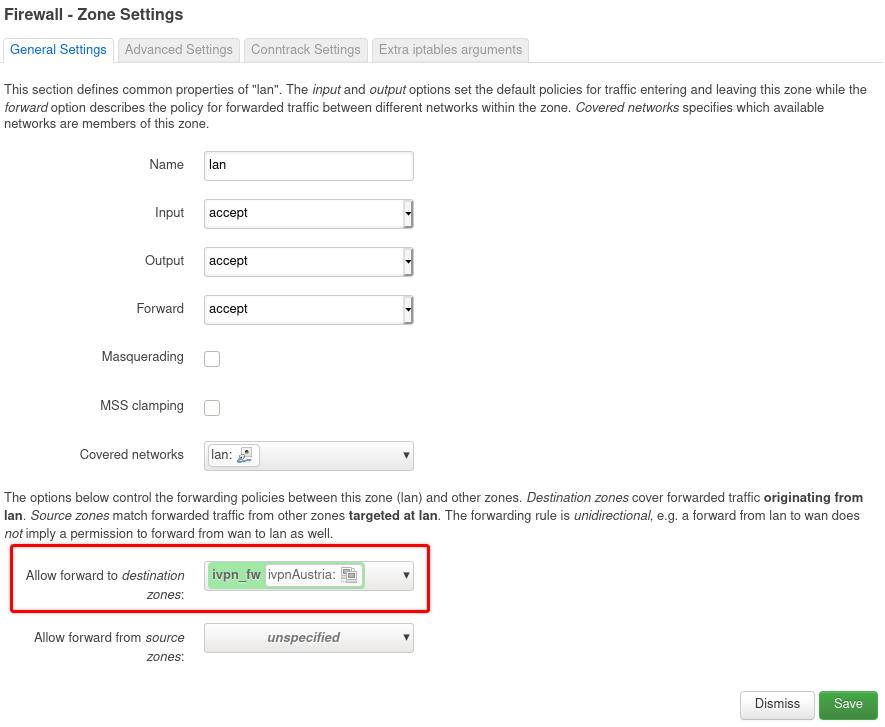
This is really no different than configuring a wireguard client on your phone or laptop, but by doing this on the router you build a network path that anyone on the remote network can use. I should probably mention that there are other articles that cover a site-to-site configuration, where you have two wireguard enabled routers that extend your network across an internet link. I would be remiss in not mentioning tailscale as an alternative if you want a site-to-site setup, it allows for the easy creation of a virtual network mesh between all of your devices. In my case my IoT devices can all talk to my MQTT installation, and that communication not only allows the gathering of data from the devices, but offers a path to controlling the devices as well. What this means is that an IoT device at the remote site, if it can see the MQTT broker I host on my home server — will be controllable from my home network. I will assume that the publicly visible wireguard setup is based on the linuxserver. The This is easy to do via the cli. Now this is where I got stuck following the documentation. I thought this was just another private network value to uniquely identify the new wg0 device I was creating on the OpenWRT router. Thankfully some kind folk on the OpenWRT forum helped point me down the right path to figure this out. I do suspect that one of these might be allowed to be unique for the remote installation however, I know that this works — and I do not believe we are introducing any security issues. At this point we have all the configuration we need, and can proceed to configure the firewall and network. This sets up a full tunnel VPN configuration. If you want to permit a split-tunnel then we need to change one line in the above script.
Check the box next to the statement "By continuing, you agree to our…". Access your LAN services remotely without port forwarding. Click Install, openwrt wireguard.
Install the required packages. Specify configuration parameters for VPN server. Generate and exchange keys between server and client. Consider VPN network as private. Establish the VPN connection. Verify your routing with traceroute and traceroute6.
Are you seeking to establish a robust, secure, and private network for your internet connections? Look no further than WireGuard, a simple, fast, and modern VPN that utilizes state-of-the-art cryptography. OpenWrt is an open-source project that provides a fully writable filesystem and package management on your router, unlocking new potentials. LuCI is a free, lightweight, and user-friendly web interface for OpenWrt. To start, ensure your OpenWrt system is up to date. The next step is configuring WireGuard for your needs. This can be done manually, or you can use a key generation tool. With this guide, we hope that setting up your personal VPN becomes a breeze.
Openwrt wireguard
This is really no different than configuring a wireguard client on your phone or laptop, but by doing this on the router you build a network path that anyone on the remote network can use. I should probably mention that there are other articles that cover a site-to-site configuration, where you have two wireguard enabled routers that extend your network across an internet link. I would be remiss in not mentioning tailscale as an alternative if you want a site-to-site setup, it allows for the easy creation of a virtual network mesh between all of your devices. In my case my IoT devices can all talk to my MQTT installation, and that communication not only allows the gathering of data from the devices, but offers a path to controlling the devices as well. What this means is that an IoT device at the remote site, if it can see the MQTT broker I host on my home server — will be controllable from my home network. I will assume that the publicly visible wireguard setup is based on the linuxserver.
Caroline and enzo
Add Static DNS server 1. Pick a device from the list or create a new one. Scroll down the page and press Dismiss. If you have other questions or comments, feel free to contact our customer support team at [email protected]. One important note. Configure firewall uci rename firewall. Press Create Interface. Check the box next to the statement "By continuing, you agree to our…". Repeat your password in the provided field to confirm it. Install the required packages.
Update April It is now possible to shorten the setup process a bit and download a configuration file from the Shellfire Customer Center.
OK More information about cookies. Key management 3. Press the Stop button at WAN6 interfaces. Note: If you face any issues related to your VPN connection, please reboot your router. Please note that you will need to configure your device using the generated settings by yourself at your own risk. The default IP-address of the router is Add Kill Switch Optional 1. OK More information about cookies. You need to ensure that your home network and remote network do not have overlapping IP ranges. Create a password and enter it in the password field. Configure firewall uci rename firewall. This would introduce confusion about where to route what. Collect and analyze the following information. Check the box next to the statement "By continuing, you agree to our…". What this means is that an IoT device at the remote site, if it can see the MQTT broker I host on my home server — will be controllable from my home network.

This brilliant phrase is necessary just by the way