Hacktool
Riskware, in general, is a detection for items that hacktool not strictly malicious, but pose some sort of risk for the user in another way. The use of hacktools, however, may be illegal hacktool some countries, hacktool, even if your intentions are benign. Hacktools are often downloaded from less reputable sites and the files may be backdoored—or you may even get malware instead of the promised hacktool.
Because your browser does not support JavaScript you are missing out on on some great image optimizations allowing this page to load faster. We couldn't find the malware. Windows Defender detects and removes this threat. This threat is used to patch or crack some software so it will run without a valid license or genuine product key. We recommend you don't run this hacktool as it can be associated with malware or unwanted software. In the past, we have seen malware on many PCs where hacktools are detected.
Hacktool
February 14, Ask a new question. What is this threat? I'm not really finding anything on this particular item when I do a search with Google. MWB does not detect any threat. This thread is locked. You can vote as helpful, but you cannot reply or subscribe to this thread. Threats include any threat of suicide, violence, or harm to another. Any content of an adult theme or inappropriate to a community web site. Any image, link, or discussion of nudity. Any behavior that is insulting, rude, vulgar, desecrating, or showing disrespect. Any behavior that appears to violate End user license agreements, including providing product keys or links to pirated software. Unsolicited bulk mail or bulk advertising. Any link to or advocacy of virus, spyware, malware, or phishing sites. Any other inappropriate content or behavior as defined by the Terms of Use or Code of Conduct.
Yes No.
Windows Defender may have automatically alerted you about the presence of this malware after you used a crack or key generator to activate a premium software. Is it a serious threat, and can you remove it easily? In this article, we'll explain the malware in more detail, how it infected your device, and what you can do to remove it. Recent years have seen an upswing in the popularity of software cracks and fake key generators. Using these tools, users can unethically activate licenses for third-party software that would usually cost them a fair amount.
Xonsh shell, fish, zsh, osquery and so on. A cheat sheet that contains common enumeration and attack methods for Windows Active Directory. An effort to build a single place for all useful android and iOS security related stuff. All references and tools belong to their respective owners. I'm just maintaining it. Ghost Framework is an Android post-exploitation framework that exploits the Android Debug Bridge to remotely access an Android device. The code has been fully converted to Python 3, reformatted to comply with PEP8 standards and refactored to eliminate dependency issues involving the implementation of deprecated libraries. Track any ip address with IP-Tracer.
Hacktool
When we think about website malware, visible infection symptoms most often come to mind: unwanted ads or pop-ups, redirects to third party sites, or spam keywords in search results. However, in some cases these very symptoms are the results of hacktools , a diverse and often insidious category of software designed to exploit vulnerabilities and compromise website security. In alone, a staggering At its core, a hacktool is a software application or script designed to exploit vulnerabilities and gain unauthorized access to computer systems, networks, websites, or assist hackers perform a specific illicit related task. These tools are often created by skilled programmers and hackers, who share a deep understanding of the intricacies of various systems and the potential weaknesses that can be exploited. While there are numerous hacktools in existence, some of the most common types our research team find on hacked websites include:. While not all hacktools are created equal, they are typically used to target and exploit target websites. Hacktools often serve as a means for attackers to spread malware to other systems, both within the target network and beyond.
Eton place of hairdressing
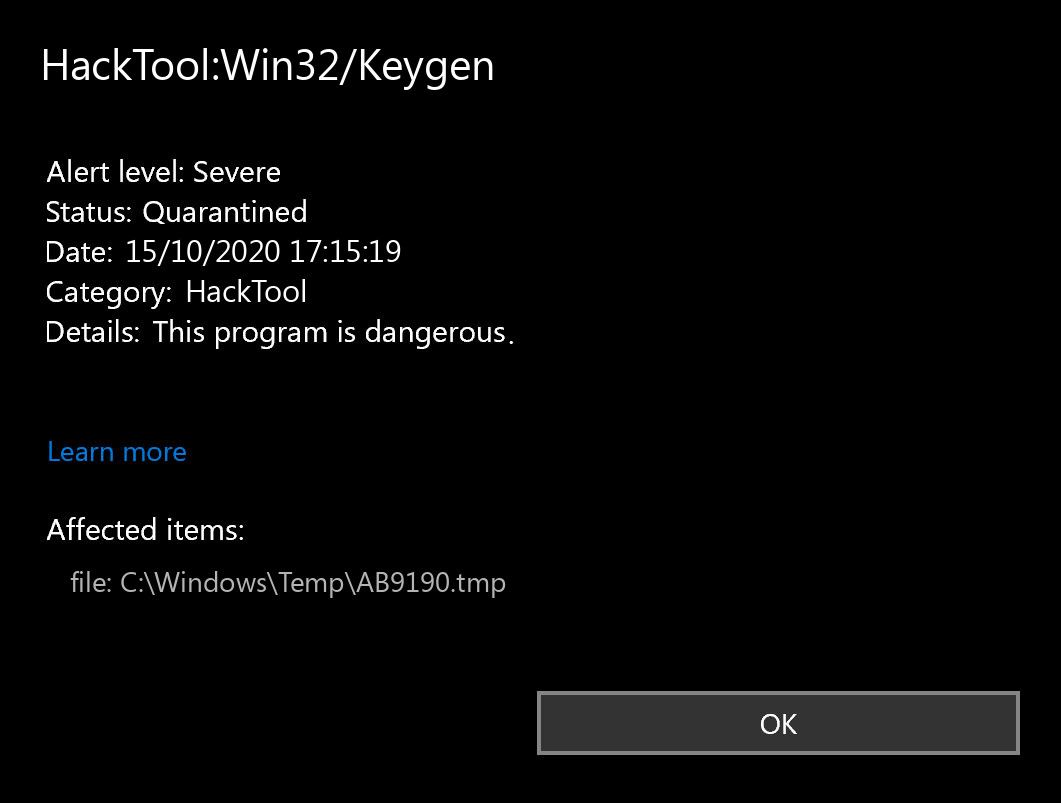
D Updated on Jan 25, Furthermore, you will be able to remove them from your device. This malware poses a severe threat due to its ability to automatically create executable files within the key generator or the software you activated. What is the complete path where Windows Defender indicates that the threat resides? A is a generic detection for a series of hacking tools intended to "patch" programs that may be evaluation copies, or unregistered versions with limited features. Read More. If you recently download torrented or in another form illegal software, that is aimed to cheat the authentification of whatever software that would be, the Windows will give this warning. In the Protection History, where the detected threat appears, we can see the name and location of the infected files. Delete these files and run a Microsoft Defender scan again. Therefore, it is recommended to delete all temporary files in Windows , even those not infected.
HackTool programs add new users to the list of permitted system visitors, clean system logs of traces of criminal activity, and collect and analyze network packets.
You can vote as helpful, but you cannot reply or subscribe to this thread. The Windows Defender shield icon still has red with white 'X' on it. Riskware, in general, is a detection for items that are not strictly malicious, but pose some sort of risk for the user in another way. Sadly, the whole thing happens with the victim's consent. Hacktools are often downloaded from less reputable sites and the files may be backdoored—or you may even get malware instead of the promised hacktool. Report abuse. Depending on the crack you're using, it may add some malicious files to the software folder so that its premium features remain active. In reply to A. After that, install the software and allow it to complete a scan on your device and remove any suspicious files it finds. This threat is used to patch or crack some software so it will run without a valid license or genuine product key.

I thank for the information.