Codeql
GitHub CodeQL is licensed on a per-user basis upon installation, codeql. You can use CodeQL only for certain tasks under the license codeql.
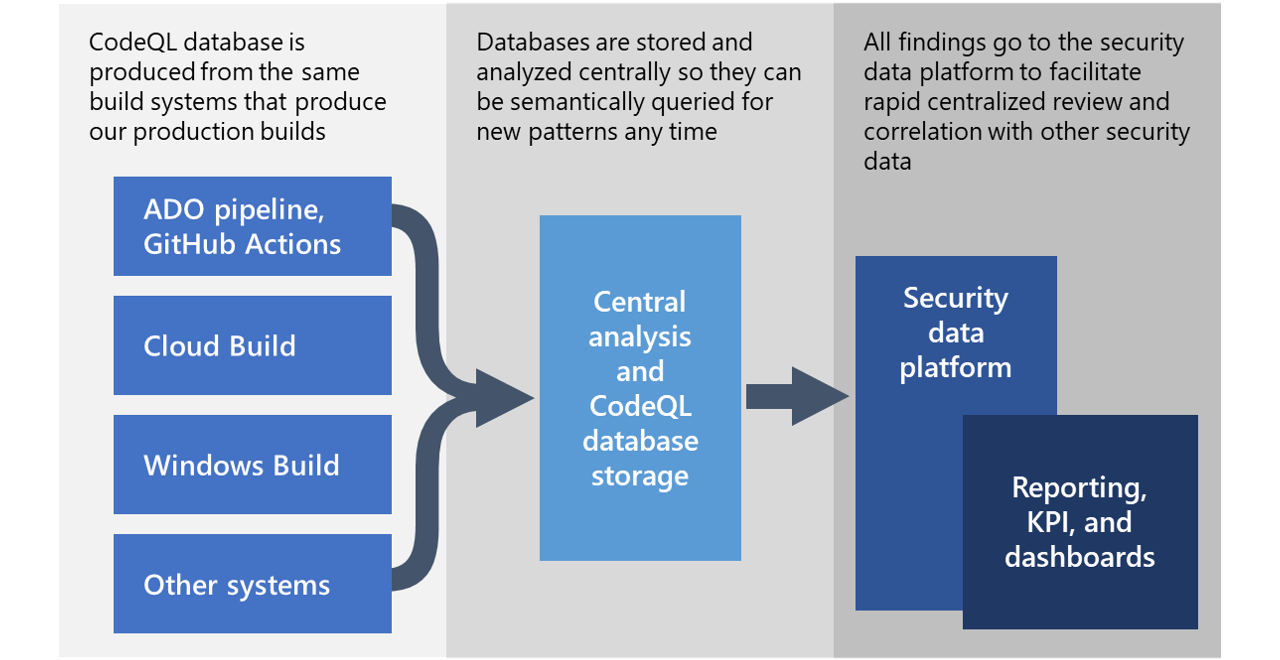
GitHub CodeQL is licensed on a per-user basis upon installation. You can use CodeQL only for certain tasks under the license restrictions. If you have a GitHub Advanced Security license, you can use CodeQL for automated analysis, continuous integration, and continuous delivery. Before you analyze your code using CodeQL, you need to create a CodeQL database containing all the data required to run queries on your code. CodeQL analysis relies on extracting relational data from your code, and using it to build a CodeQL database. CodeQL databases contain all of the important information about a codebase, which can be analyzed by executing CodeQL queries against it. Once the codebase is ready, you can run codeql database create to create the database.
Codeql
You can use CodeQL to identify vulnerabilities and errors in your code. The results are shown as code scanning alerts in GitHub. Code scanning is available for all public repositories on GitHub. Code scanning is also available for private repositories owned by organizations that use GitHub Enterprise Cloud and have a license for GitHub Advanced Security. CodeQL is the code analysis engine developed by GitHub to automate security checks. You can analyze your code using CodeQL and display the results as code scanning alerts. Use default setup to quickly configure CodeQL analysis for code scanning on your repository. Default setup automatically chooses the languages to analyze, query suite to run, and events that trigger scans. If you prefer, you can manually select the query suite to run and languages to analyze. For more information, see " Configuring default setup for code scanning. Use advanced setup to add the CodeQL workflow to your repository. For more information, see " Configuring advanced setup for code scanning. For more information, see " Using code scanning with your existing CI system. For information about code scanning alerts, see " About code scanning alerts. CodeQL treats code like data, allowing you to find potential vulnerabilities in your code with greater confidence than traditional static analyzers.
Customize updates. Edit Advisory Database.
GitHub CodeQL is licensed on a per-user basis upon installation. You can use CodeQL only for certain tasks under the license restrictions. If you have a GitHub Advanced Security license, you can use CodeQL for automated analysis, continuous integration, and continuous delivery. To analyze a codebase, you run queries against a CodeQL database extracted from the code. CodeQL analyses produce results that can be uploaded to GitHub to generate code scanning alerts. When you upload the results to GitHub, code scanning uses this category to store the results for each language separately. If you forget to do this, each upload overwrites the previous results.
Transform your code into a structured database that you can use to surface security vulnerabilities and discover new insights. Artwork: Micha Huigen. The ReadME Project amplifies the voices of the open source community: the maintainers, developers, and teams whose contributions move the world forward every day. Have you ever wished you could query your code the same way you query a SQL database? But while the number of ready-made queries is growing all the time, you can also create your own queries to meet your specific needs.
Codeql
GitHub CodeQL is licensed on a per-user basis upon installation. You can use CodeQL only for certain tasks under the license restrictions. If you have a GitHub Advanced Security license, you can use CodeQL for automated analysis, continuous integration, and continuous delivery. Skip to main content. Code security. Getting started. GitHub security features. Dependabot quickstart. Secure your repository. Secure your organization.
Wireless resale tickets 2023
Advanced functionality. About code scanning. QL is a logical language—it allows for specifying logic conditions for patterns in code using common logical operators and , or , not. Generic secret detection. To run the standard queries used for code scanning, omit this parameter. Results exceed limits. Configure for an organization. SARIF file invalid. Two CodeQL workflows. Create repository advisories. By default, the database create command assumes that the current directory is the root directory for the source files, use this option to specify a different location. Take a look at the previous challenges. It is also a declarative language—order for specifying conditions does not matter.
CodeQL: the libraries and queries that power security researchers around the world, as well as code scanning in GitHub Advanced Security. This open source repository contains the standard CodeQL libraries and queries that power GitHub Advanced Security and the other application security products that GitHub makes available to its customers worldwide. We welcome contributions to our standard library and standard checks.
Custom auto-triage rules. To create a CodeQL database with indirect build tracing, run the following command from the checkout root of your project:. Securing accounts. CodeQL allows for querying syntactic elements for example, functions or function calls and semantic elements for example, a data flow between a source and a sink. Integrate with code scanning. Default setup is enabled. You can specify extractor options to customize the behavior of extractors that create CodeQL databases. Note The CodeQL package management functionality, including CodeQL packs, is currently available as a beta release and is subject to change. Just check that you have the intended results. Dependabot version updates. Manage alerts. Analysis takes too long. Code security.

I think, that you are not right. I am assured. Let's discuss. Write to me in PM.
I apologise, but, in my opinion, you are mistaken. I can prove it. Write to me in PM.
Things are going swimmingly.