Cisco internet edge design
For cloud-enabled enterprises, the availability of their Internet facing-infrastructure is of critical importance.
By Internet Edge, I specifically mean connecting your data center s to the Internet. For those who liked the SD-Access blog series: I have a few more SD-Access blogs fermenting in my brain and hope to be posting them after this series. Teaser: SD-Access Transit with two data centers and two pairs of fusion firewalls. There are some things to be aware of and design for. Ahem, so Internet Edge. More specifically, how you design the Internet connectivity in a data center or two. Lots of double devices.
Cisco internet edge design
Updated: Nov 2, Ready to live on the edge? In the last design post we talked about remote access VPN, but in this 4th installment of the network design scenario series we will take a detailed look at designs for the network edge. What is the network edge? The network edge is where your network and outside networks connect. In the enterprise world this is your path out to the internet, in the provider world this is generally where you connect to upstream providers or peers. We will cover high and low level designs, different types of topologies such as SMB, enterprise and service provider SP , look at the building blocks, redundancy options and other considerations. How do I fail over? I feel this is probably one of the less understood areas of networks for a lot of folks, perhaps because Border Gateway Protocol BGP is very integral to it. Some might struggle with how to perform fail over properly or there are just critical details that are often overlooked.
Attacks can render a company inaccessible from the Internet and prevent employees from being productive. Cisco Secure Malware Analytics.
The Secure Edge is a place in the network PIN where a company connects to the public Internet, service providers, partners, and customers. As internal company users reach out to websites, use email and other collaboration tools, and as remote workers and customers reach in, the services of the network must remain both accessible and secure. SAFE simplifies security by starting with business flows, then addressing their respective threats with corresponding security capabilities, architectures, and designs. SAFE provides guidance that is holistic and understandable. Business Flows. The Secure Edge does not have local users; it is the main security choke point between the internal company and external users.
For cloud-enabled enterprises, the availability of their Internet facing-infrastructure is of critical importance. Cisco found that an average enterprise uses cloud services. Even relatively short Internet outages will adversely impact mission-critical cloud workloads. This results in significant costs and damage to reputations. Many enterprises may be unaware of just how significant their internet services have become to their overall business viability. The aim of this post is to outline four 4 alternate internet designs that address the shortcomings of a single unreliable internet link.
Cisco internet edge design
Use our validated guides to design your SD-WAN and deliver a great user experience for branches and remote sites. Skip to content Skip to search Skip to footer. Contact Cisco Get a call from Sales. Featured guides. WAN security Set up pervasive security policies to protect your network, data, and users. Internet edge The gateway to the Internet needs to be more agile and secure in the digital age.
Hdrip o hd 720p
That probably doesn't justify a whole other pair of high-end switches for the DMZ. If L2, do the IGP routing through it. This methodology is the preferred way for communication at the network edge. Redirection of session to malicious website. The Edge is often the first point of attack and is subsequently the first line of defense. Speaking of announcements, how will the outside networks or internet know how to reach you? As you can image though utilizing internet endpoints like DNS servers to gauge the health of your connection works, it doesn't mean that's the best way. Its provides just enough to cover multiple scenarios and is a proven design, but it isn't too complex. What is good about this is that the route-map is what is applied in the configuration, so editing the prefix list is simpler if things are structured well. Zero-day malware and attacks. Continuing, looking at the above diagram we see Azure and Lumen connections shown on each side of the diagram which could be completely different geographic regions.
.
Next we will look at the various high level edge connection examples. The code should be mature. Firewall: Stateful filtering and protocol inspection between segments in the data center. Its provides just enough to cover multiple scenarios and is a proven design, but it isn't too complex. Fiber networks are -generally- newer and have better equipment running them and are preferred over coax broadband or fixed wireless networks. Malware Sandbox:. They are the routers shaded in red shown in Figure 1. You probably will want diversity between these connections so a failure isn't shared between them. You could let traffic flow in and out based on what routes are preferred from which provider on your routers. The network edge is where your network and outside networks connect. Seizure of infrastructure or devices. You will learn how to configure and deploy feature and device templates, how to onboard WAN Edge devices, and how to configure localized and centralized policies, QoS, and application-aware routing. Compromised email, web proxies, or DNS name services enable traffic interception and redirection with out the knowledge of the parties. The reality is that if you have one site and one ISP getting truly basic , then do you invest in HA pairs of other devices? We do need iBGP between the 2 border routers so they exchange the local preference information only iBGP does and will fail over to the backup path when needed and that our prefixes are still advertised to the internet.

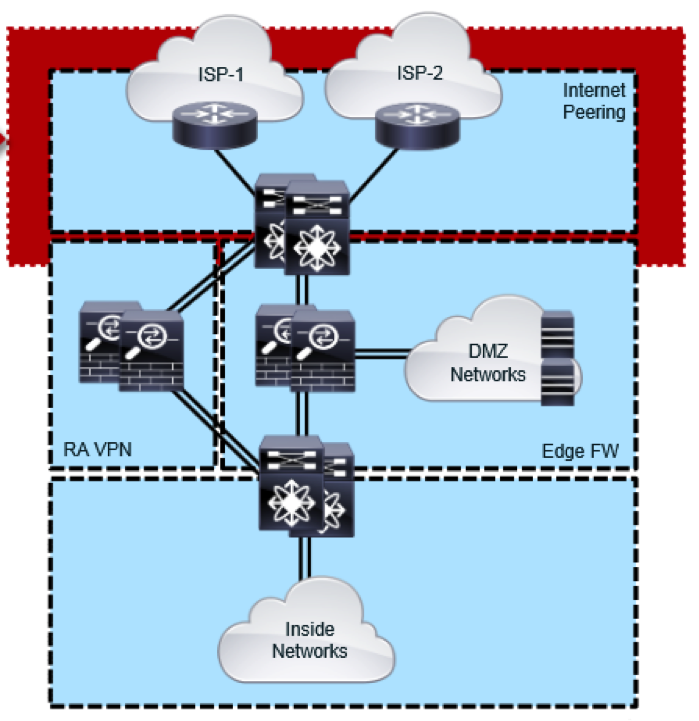
You are absolutely right.