Chainsaw rust
Chainsaw offers a generic and fast method of searching through event logs for keywords, and by identifying threats using built-in support for Sigma detection rules, and via custom Chainsaw detection rules. At WithSecure Countercept, we ingest a wide range of telemetry sources from endpoints via our EDR agent to provide our managed detection and response service. Chainsaw was created to chainsaw rust our threat hunters and incident response consultants with a tool to perform rapid triage of forensic artefacts in these circumstances, chainsaw rust. Windows event logs provide a rich source of forensic information for threat hunting chainsaw rust incident response investigations.
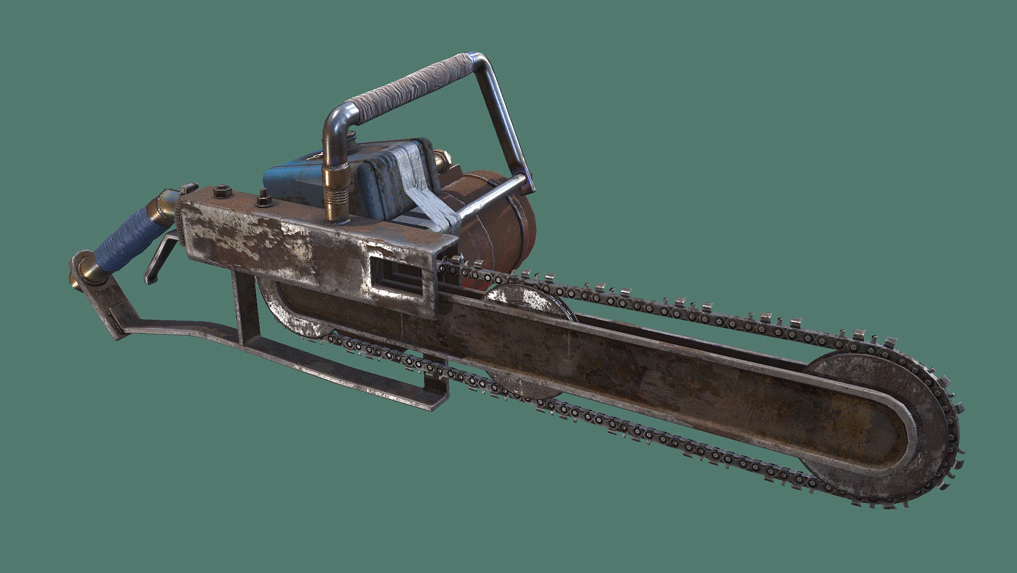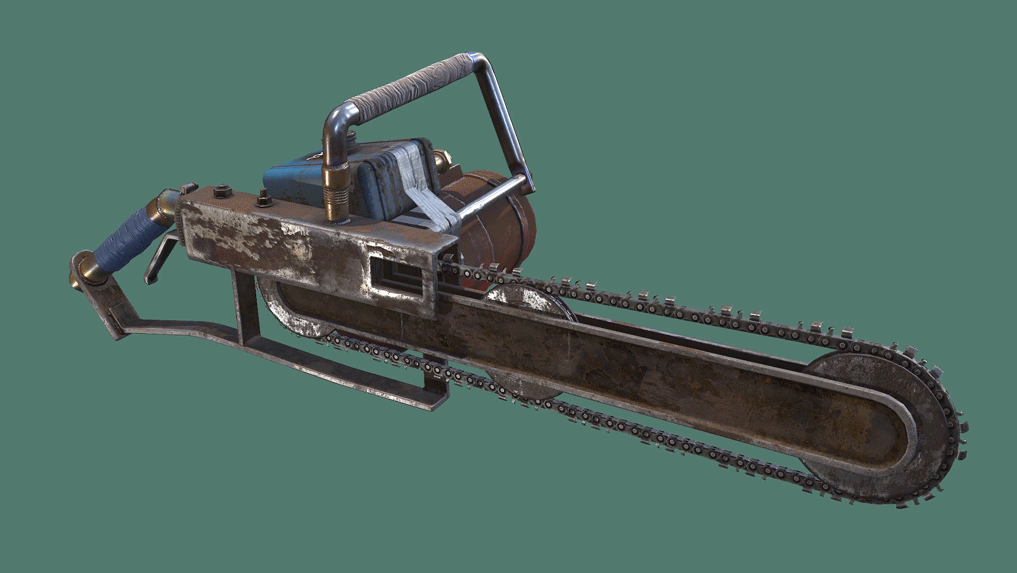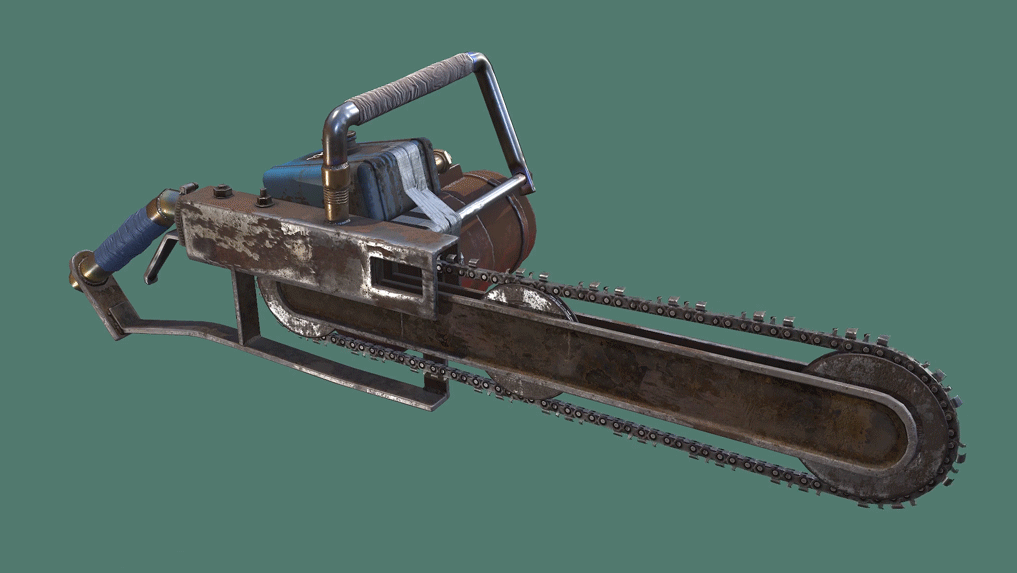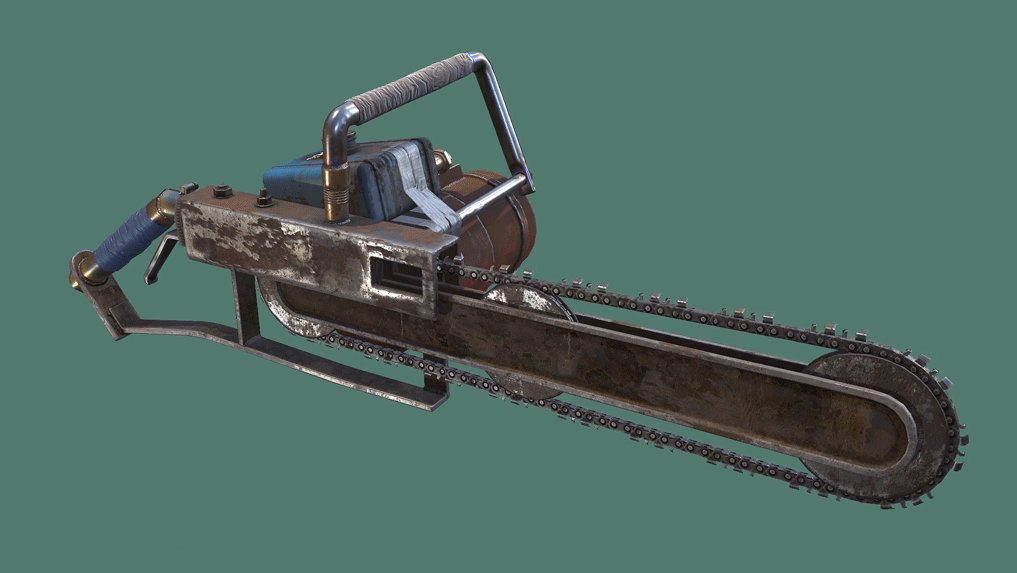
The Chainsaw is a somewhat rare harvesting tool which is an upgrade to the Hatchet and Salvaged Axe. It requires fuel to use, holding up to 50 at once, and must be revved up before it can be used. The chainsaw quickly cuts through trees, even if it doesn't hit the weak spot, and is very useful for gathering large amounts of wood quickly. The chainsaw can also be used as a melee weapon or for cutting through constructions, but beware that it loses durability very fast when doing these tasks. LittlePanda 31 pts. Biscuitius pts. Mutes all tryhard pts.
Chainsaw rust
.
Oil Rig Scientist.
.
Chainsaw offers a generic and fast method of searching through event logs for keywords, and by identifying threats using built-in support for Sigma detection rules, and via custom Chainsaw detection rules. At WithSecure Countercept, we ingest a wide range of telemetry sources from endpoints via our EDR agent to provide our managed detection and response service. Chainsaw was created to provide our threat hunters and incident response consultants with a tool to perform rapid triage of forensic artefacts in these circumstances. Windows event logs provide a rich source of forensic information for threat hunting and incident response investigations. Unfortunately, processing and searching through event logs can be a slow and time-consuming process, and in most cases requires the overhead of surrounding infrastructure — such as an ELK stack or Splunk instance — to hunt efficiently through the log data and apply detection logic. This overhead often means that blue teams are unable to quickly triage Windows event logs to provide the direction and conclusions required to progress their investigations.
Chainsaw rust
The Chainsaw is a somewhat rare harvesting tool which is an upgrade to the Hatchet and Salvaged Axe. It requires fuel to use, holding up to 50 at once, and must be revved up before it can be used. The chainsaw quickly cuts through trees, even if it doesn't hit the weak spot, and is very useful for gathering large amounts of wood quickly. The chainsaw can also be used as a melee weapon or for cutting through constructions, but beware that it loses durability very fast when doing these tasks.
Çalıkuşu 6 bölüm aydan şener
Dismiss alert. In July we released version 2 of Chainsaw which is a major overhaul of how Chainsaw operates. Biscuitius pts. Output to the terminal. Latest commit History Commits. Metal Blade Blueprint. If you still wish to use the version 1 of Chainsaw, you can find compiled binaries in the releases section , or you can access the source code in the v1. The paths containing event logs to load and hunt through. Report 1 Mutes all tryhard pts. Last commit date. Hunt through all evtx files using Sigma rules and Chainsaw rules for detection logic and output in CSV format to the results folder. Hunting Logic for Windows Event Logs. Unfortunately, processing and searching through event logs can be a slow and time-consuming process, and in most cases requires the overhead of surrounding infrastructure — such as an ELK stack or Splunk instance — to hunt efficiently through the log data and apply detection logic. Latest commit.
.
Chainsaw Detection Rules. LittlePanda 31 pts. Last commit date. We have also seen instances where the Chainsaw binary has been detected by a small subset of Anti-Virus engines likely due to some form of heuristics detection. Output to a csv file. Command Example. The goal is to avoid errors related to unknown tables. Large Beech Tree. Small Pine Sapling. Medium pile of Driftwood. Quick Start Guide. Forensic insights. The sound will attract nearby players so you'll want to disappear quickly after cutting down trees. The mapping file tells chainsaw which fields in the event logs to use for rule matching.

I think, that you are not right. I am assured. Write to me in PM.
In my opinion you are not right. I am assured. I can prove it. Write to me in PM, we will communicate.
And something similar is?